减少运维成本
90%
降低安全风险
75%
提高生产效率
50%
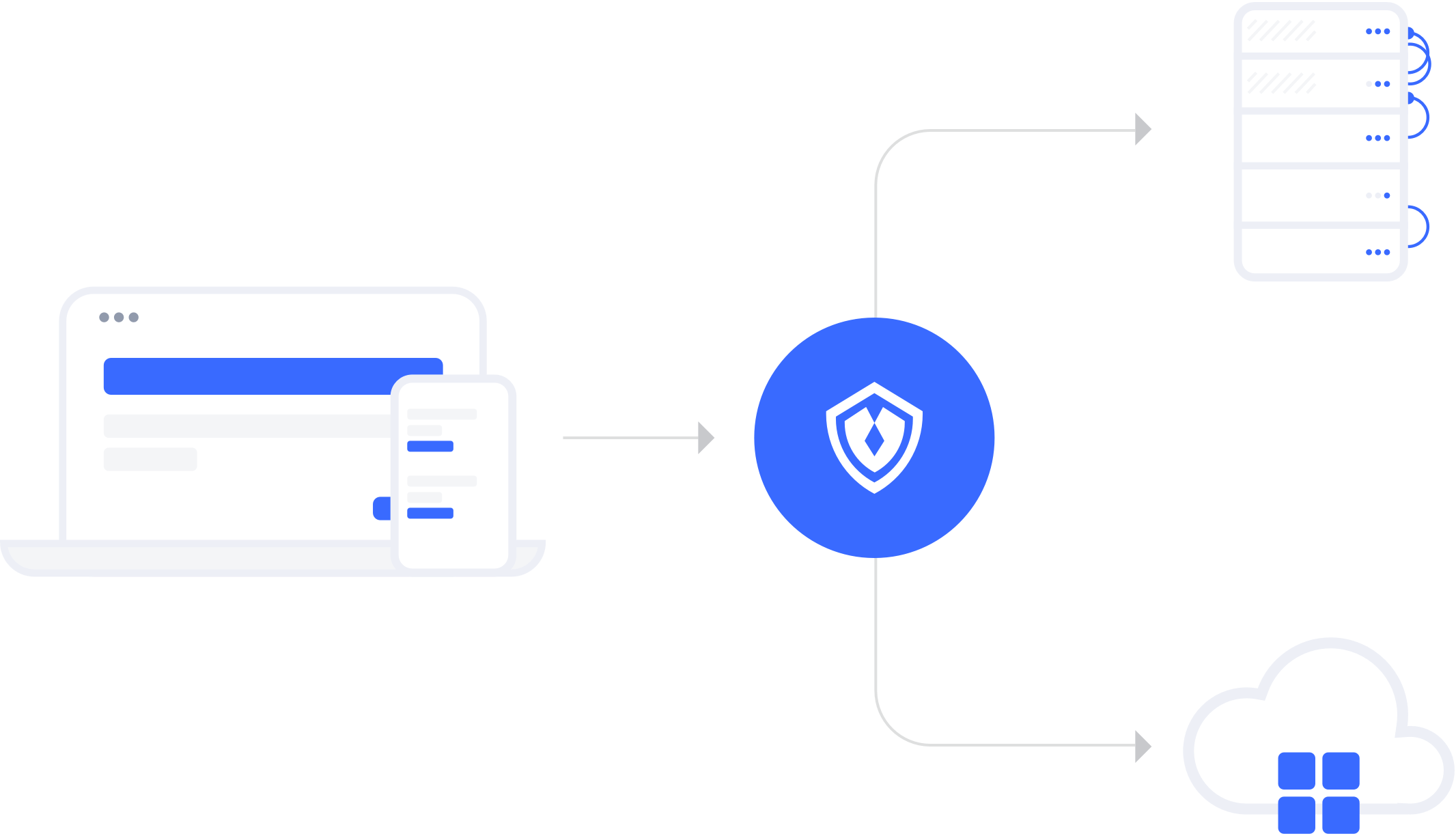
智能的安全保护,伴随应用的每一次访问管理
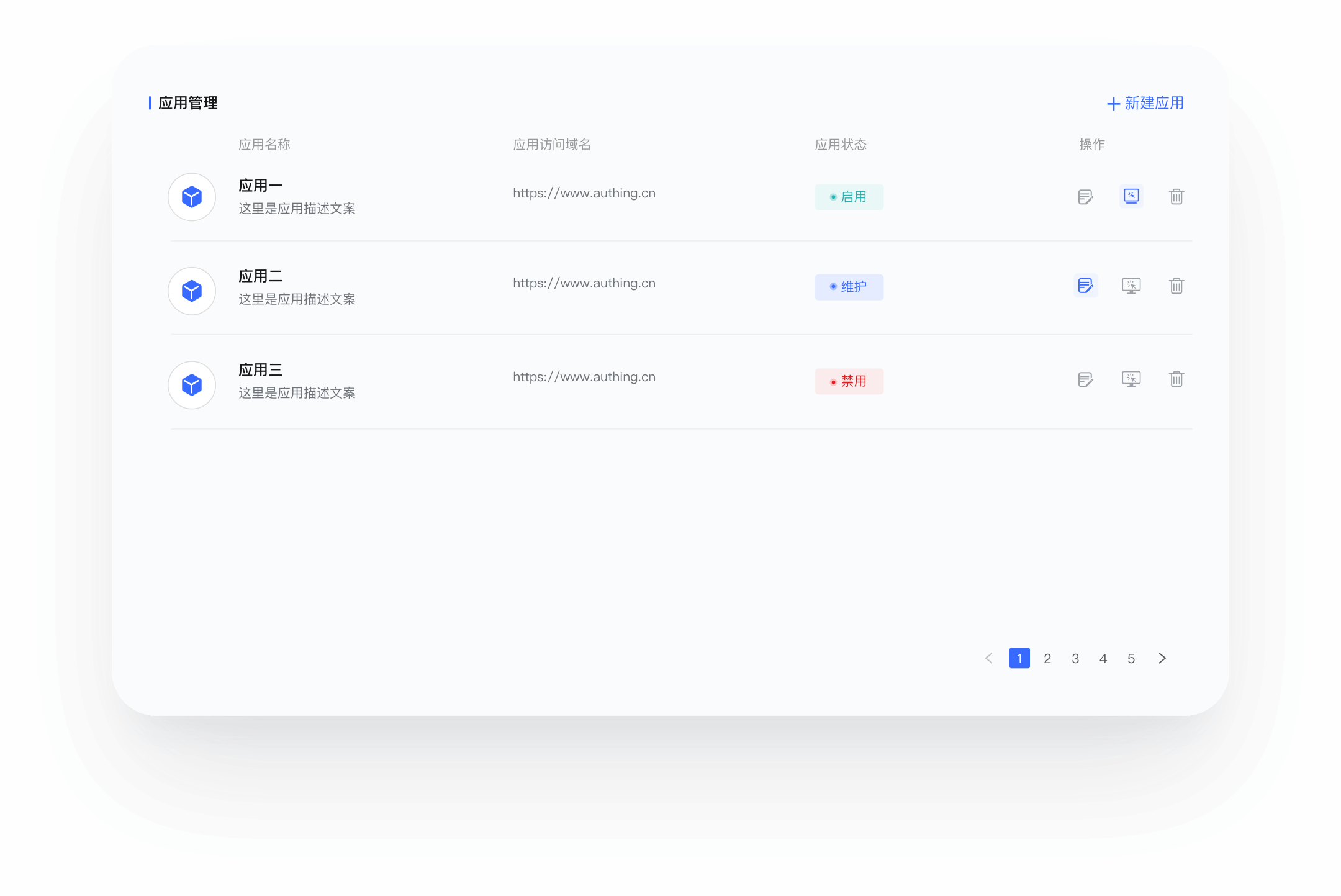
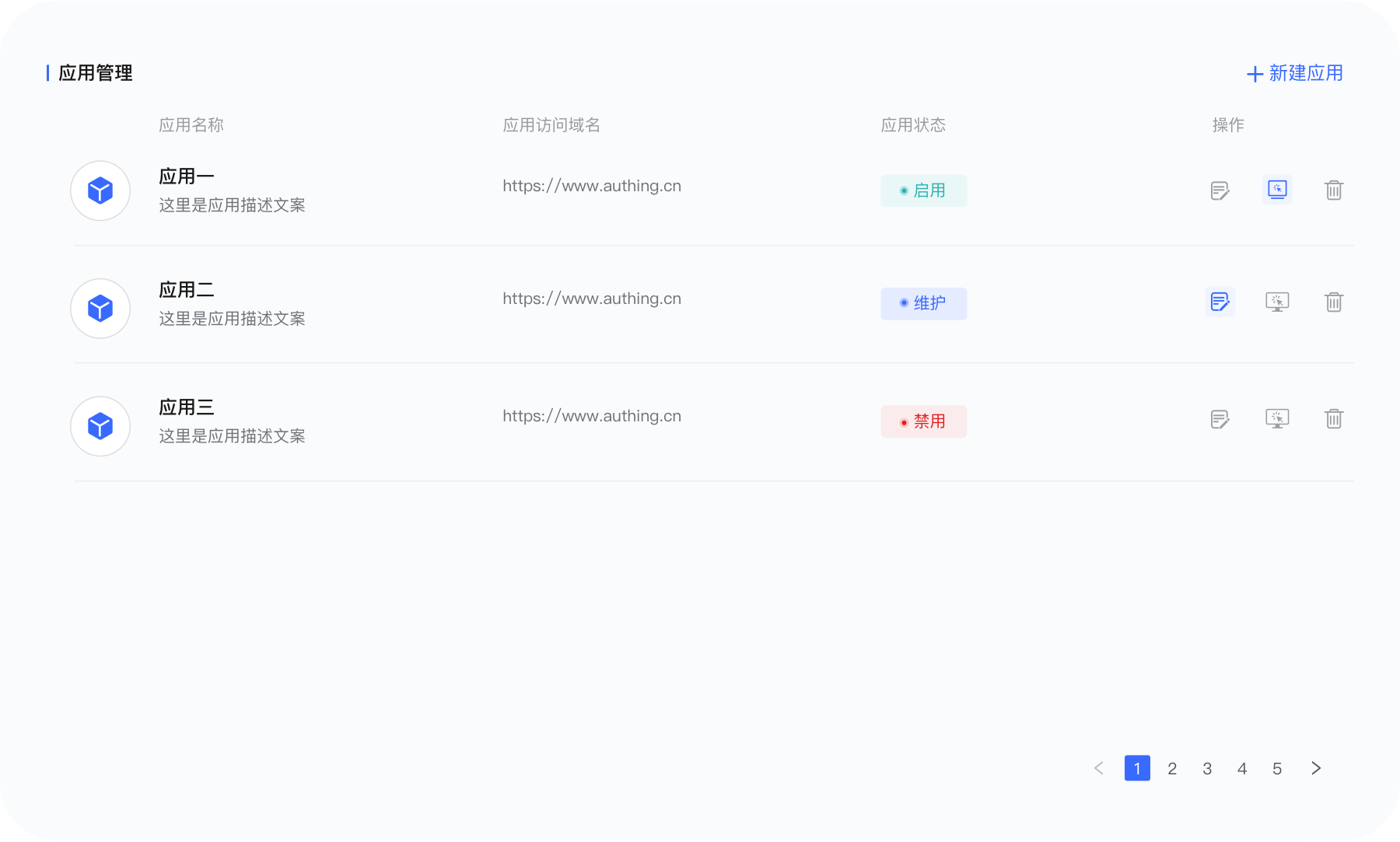
统一访问管理
你的混合云需要更安全的访问管理,通过集中访问控制,为本地应用创建高效、统一的安全策略。
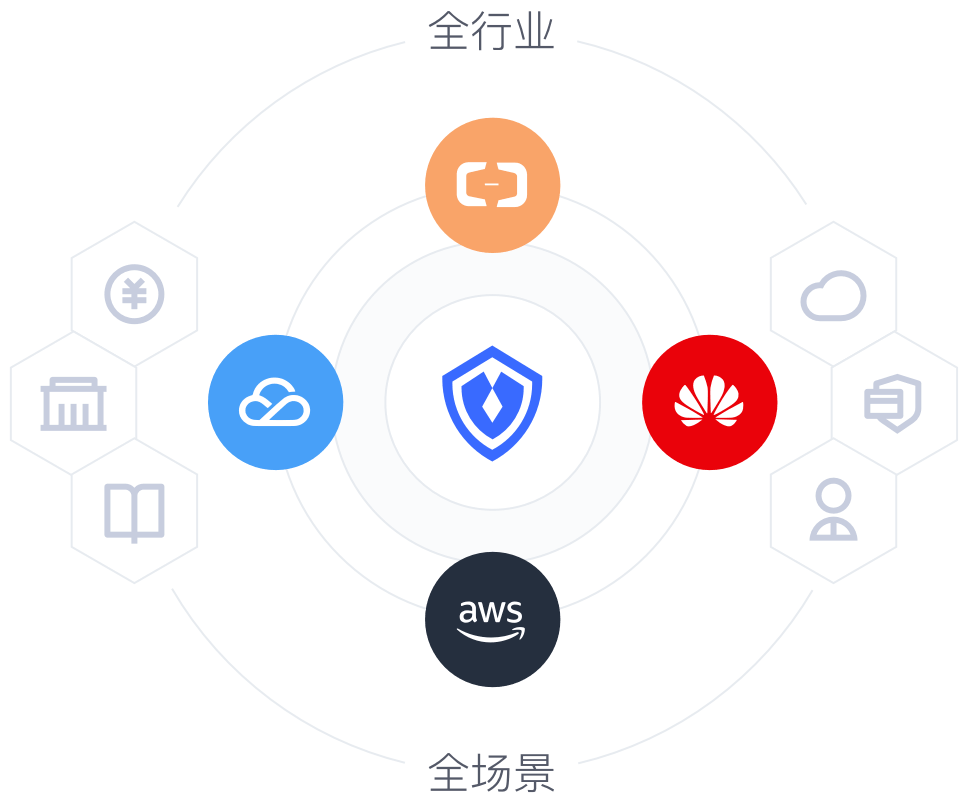
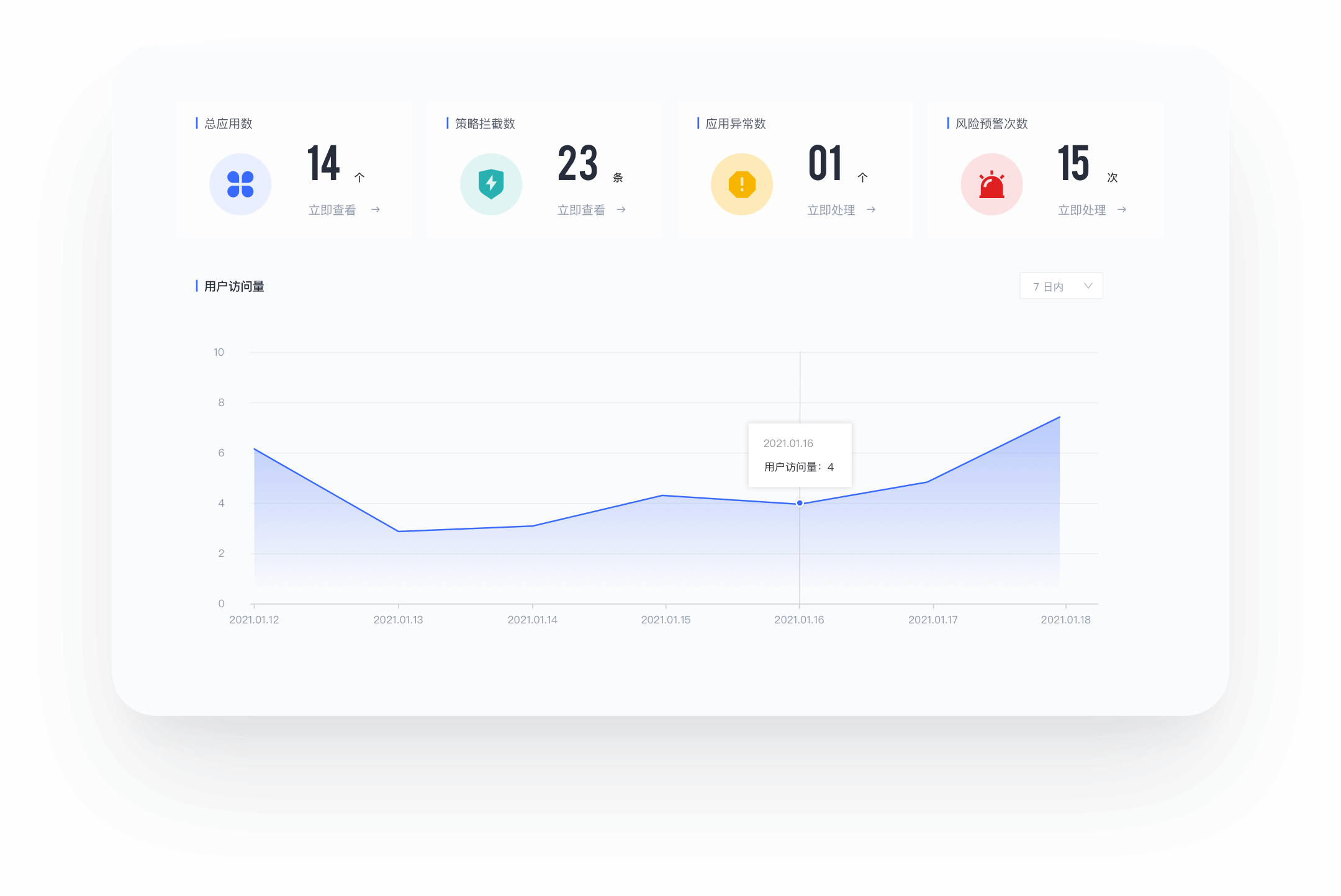
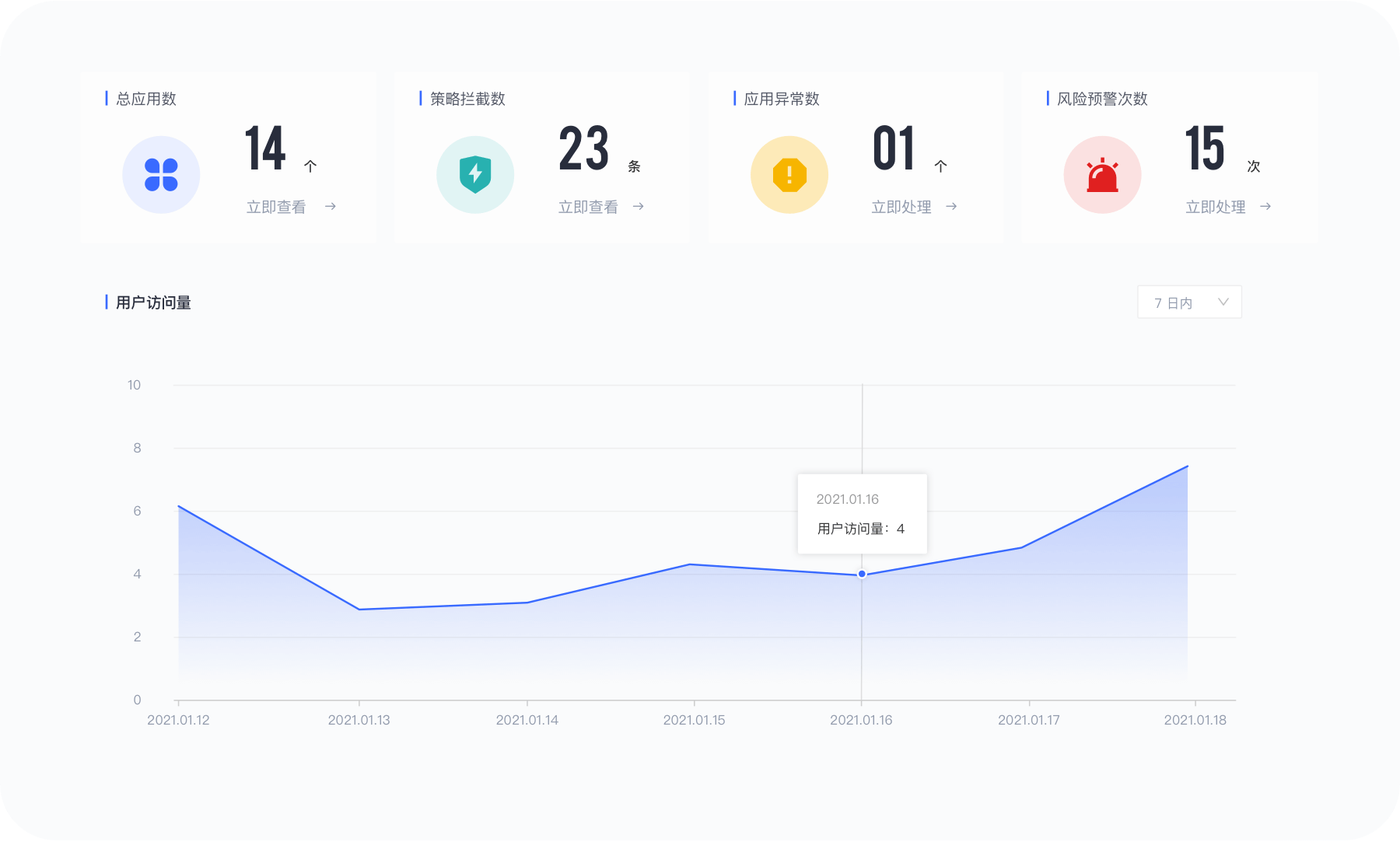
智能保护
部署在本地的应用集成网关,利用智能安全防护,为应用系统提供安全保护层。
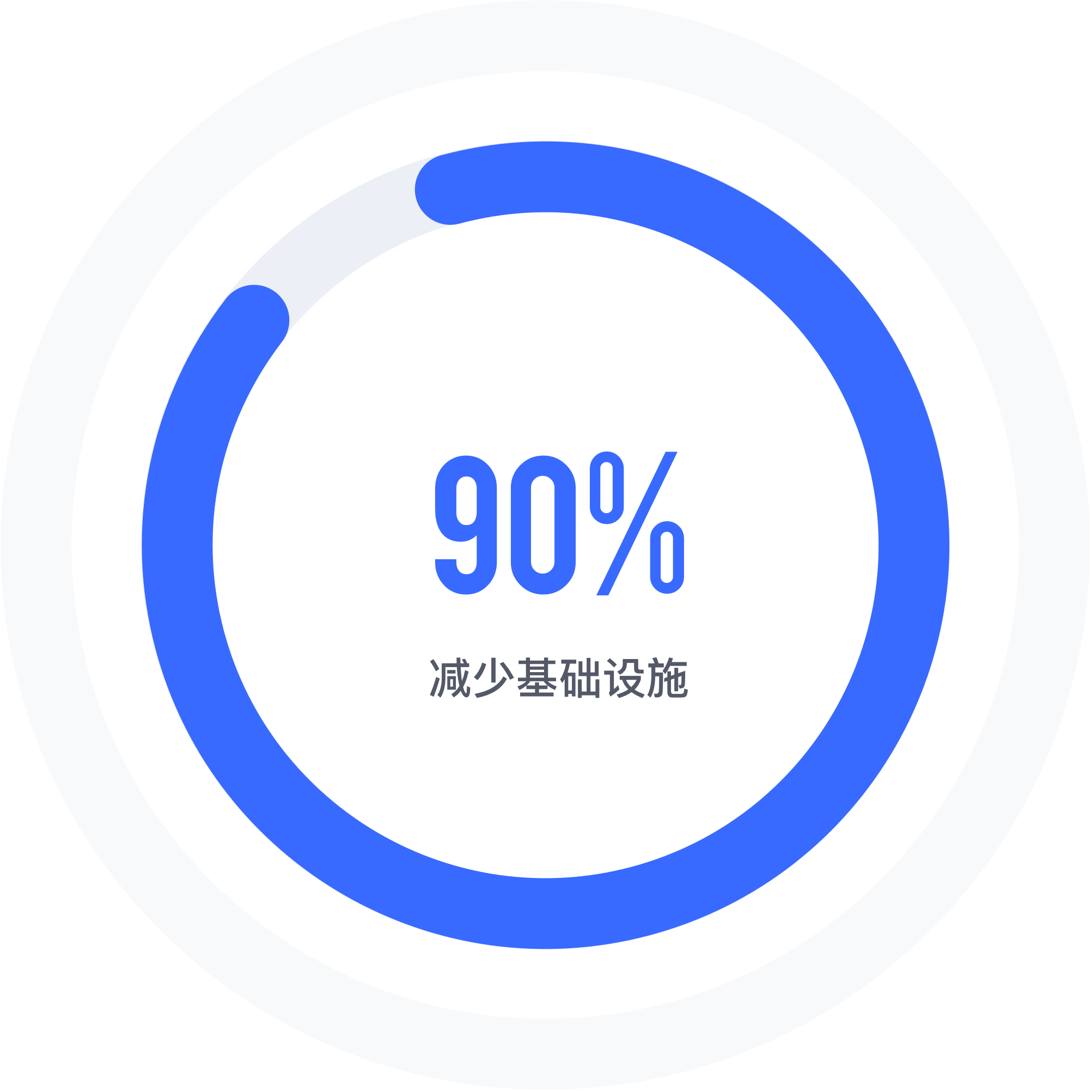
轻量级架构,低成本运维
基础设施运维成本占比的减少对于企业至关重要,应用集成网关可将身份基础设施减少 90%,意味着需要更少的计算资源和维护成本,极大降低企业运营成本,保障数据安全。
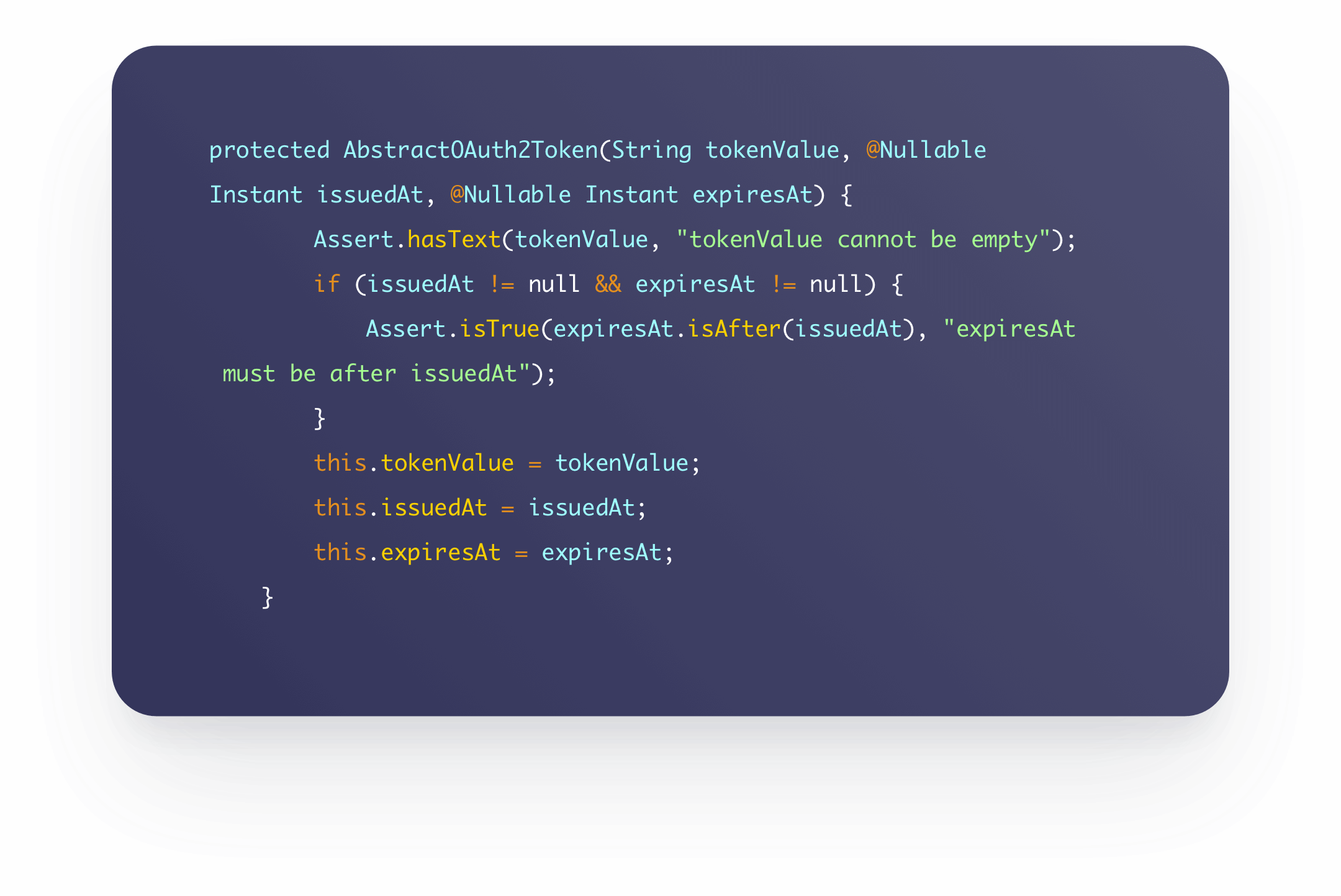
开发者友好,零代码集成
无需更改应用系统代码,就能与老应用做身份集成,快速支持数十种认证方式,省去应用集成的高成本。
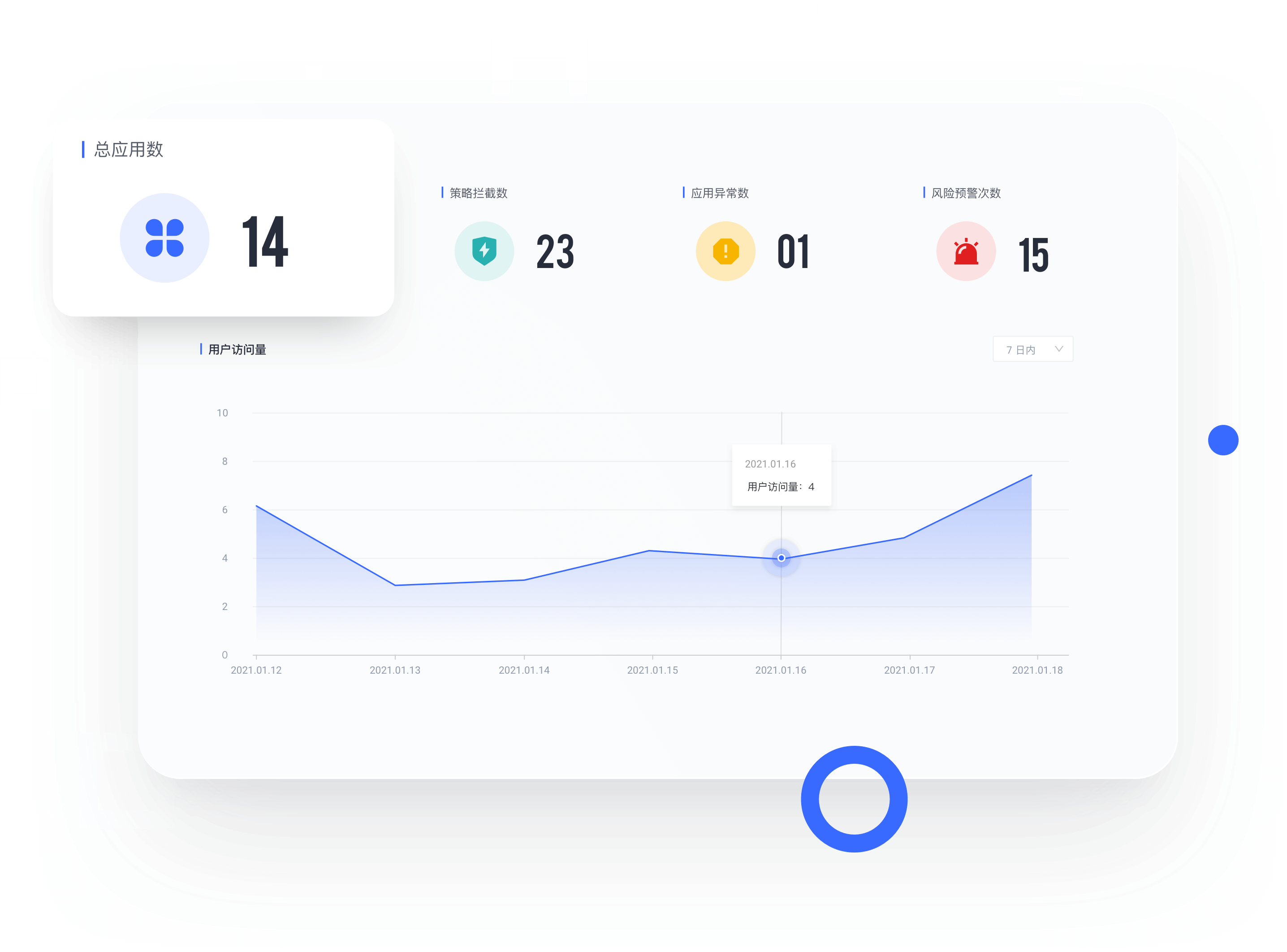
以高效功能,助你业务更上一层楼
以高效功能,助你业务更上一层楼
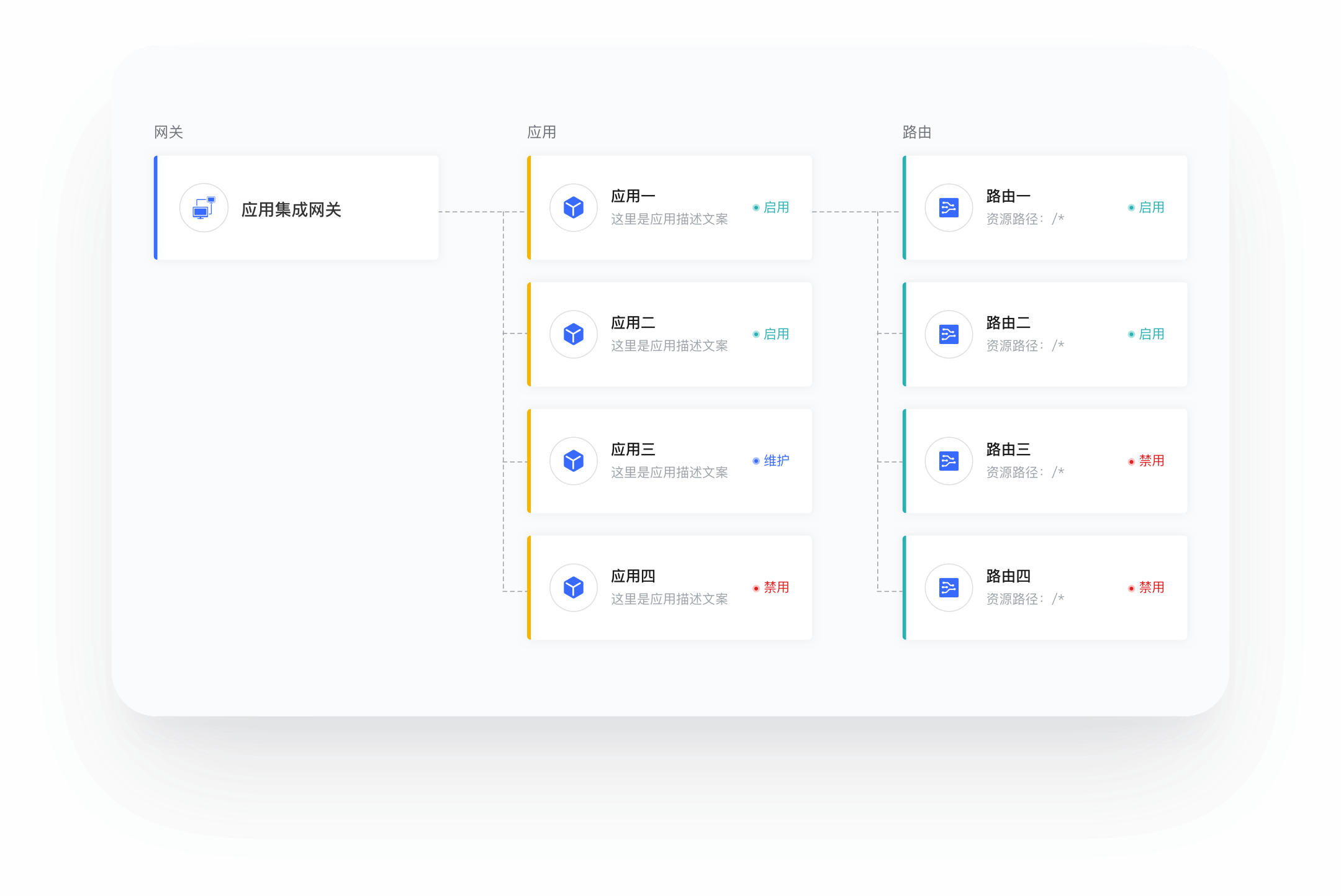
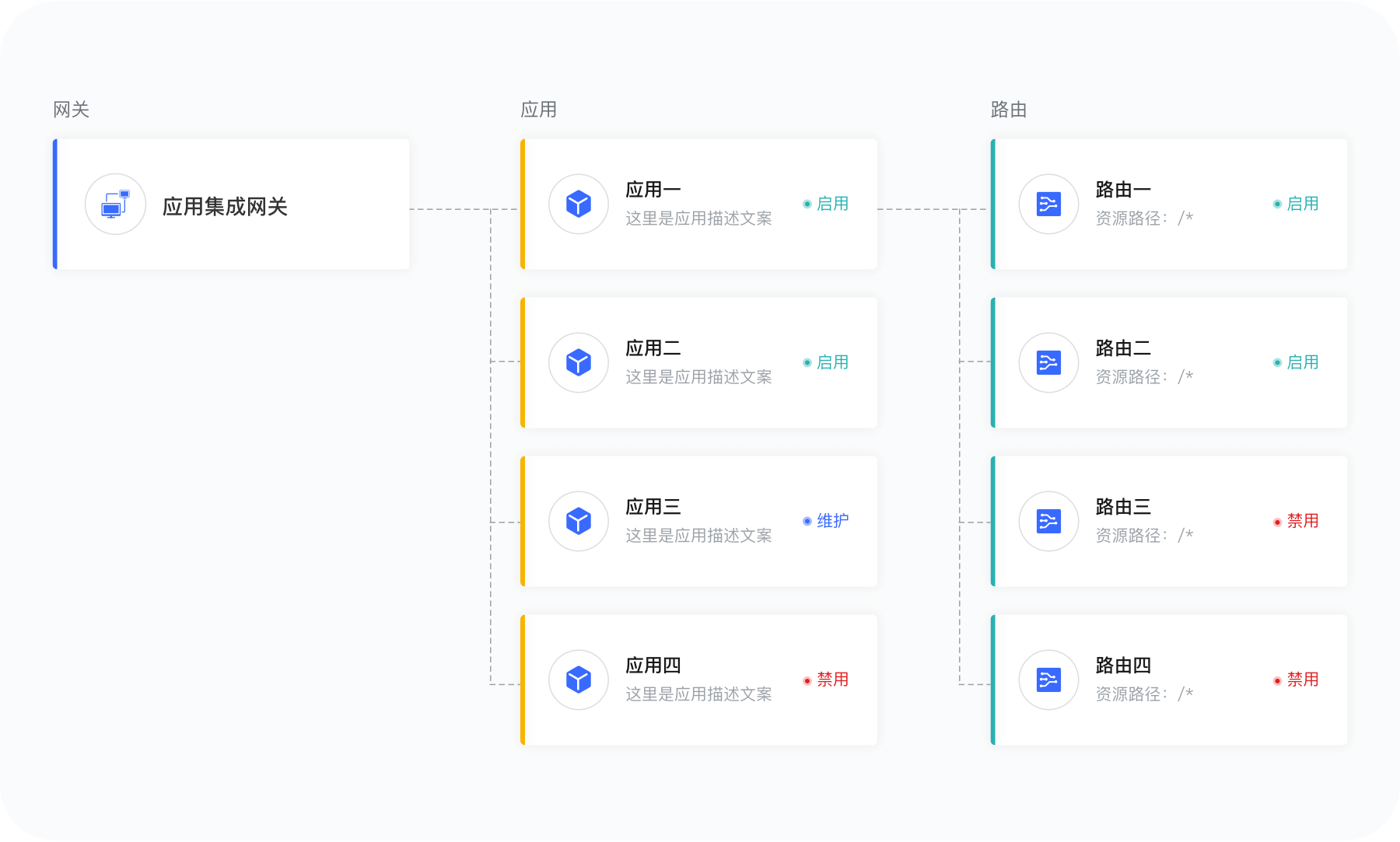
Authing 应用集成网关认证流程
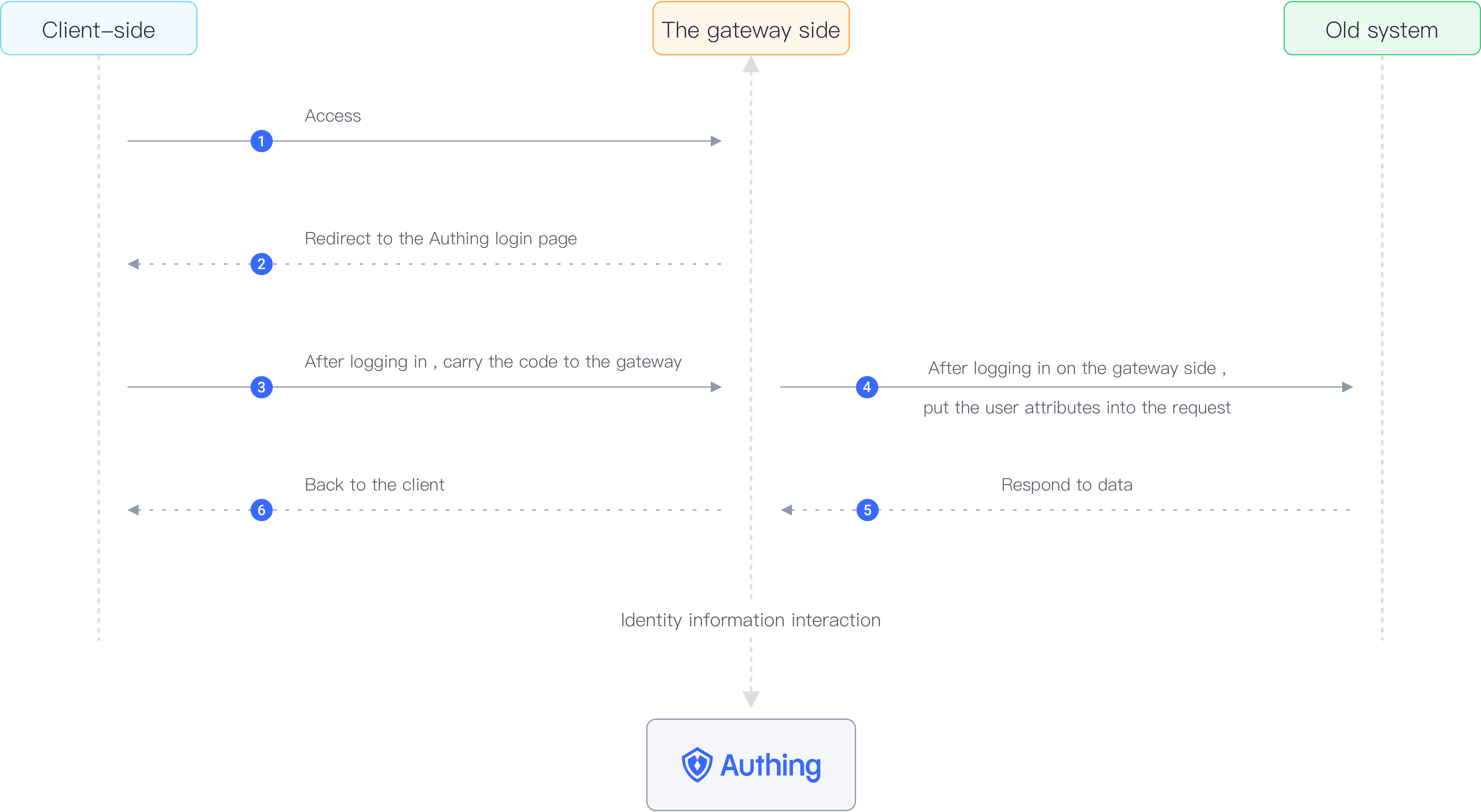
快速集成 五分钟实现
单点登录、认证授权、权限管理等功能